Comprehensive list of common crypto scams
And best practices to avoid them
These is a list of crypto scams and best practices to avoid them. They are collected from many years of posts from multiple subs (CryptoScams, CryptoScamReport, Solidity, Metamask, EthDev, Ethereum, CryptoCurrency, BinanceSmartChain, 0xPolygon), CryptoTwitter, and other Medium/Substack articles.
This article starts with the zero/low-tech methods and works its way to more technical methods towards the end. Most scams are zero/low-tech and simply use social engineering methods.
The most-technical ones are really hard to detect even for those experienced in crypto. I’ve written smart contracts to test their methods, and some would trick most users other than experienced developers.
Table of Contents
Part 1: Best Practices to keep your crypto safe
1A - Basic Best Practices
1B - Intermediate Best Practices
1C - Advanced Best Practices
Part 2: Common Scam Tactics and Vectors of Attack
2A - Preparation
2B - Vectors of Attack
Part 1: Best Practices to keep your crypto safe
1A - Basic Best Practices
Basic and super-obvious practices you should already know.
Don't use links from emails and random messages.
Always examine the URL. It could be a fake link with minor spelling errors that resembles the real one (e.g. xx.co instead of xx.com, LIi.com instead of Lli.com, or xx1.com instead of xxl.com).
Don't type in a login after clicking on a link. Instead, open a new tab and navigate to the official website's address. There are a lot of phishing scammers pretending to be MetaMask, Coinbase, Uniswap, Binance, or someone else asking you to log into a website.
Ignore private messages on social media from unknown senders about crypto, especially on Reddit if that user has less than 100 karma. Be aware of the Pigs Butchering long con.
If you ask for help on social media, you will likely get spammed by private messages pretending to be support agents. Ignore them; they’re fake.
Do NOT trust verified Twitter Blue accounts. They're meaningless and have been used in countless crypto scams (as even a veteran EthFinance victim recently discovered). Hackers steal them all the time from others, and they can change the account name and description. Even friend’s accounts may be compromised, allowing the attacker to mass spam everyone on their contact list.
No NOT interact with random dApps. There are so many NFT drainer scams, and I see reports of these scams all the time.
Be wary of ads: Ads can contain links to scam sites. Google returns ads in front of their top search results, and even those ads can contain fake links instead of the real ones.
Distrust influencers unless they're dedicated developers or researchers
There are so many sketchy influencers who are just interested in pumping-and-dumping to their followers and retail investors. Also don't trust ad sponsors. Many trustworthy media sources have used FTX as sponsors in the past.
That being said, there are some trustworthy influencers on Twitter and YouTube who are dedicated developers and researchers with deep technical expertise.
Don’t be greedy: Most scams are targeting greedy people looking for a quick profit. If it seems too good to be true and no one else is talking about it, it’s probably a scam. Check with an expert first.
Don’t buy new and low-market cap tokens: There are thousands of random shitcoin being created annually, and 99% of them are scams or rug pulls. If it’s not in the top 100, you better know what you’re doing.
Split your hot and cold wallets:
It’s impossible to never make a mistake. Splitting your hot and cold wallets reduces the chances of a mistake.
Keep your hot wallet (used for interacting with others and applications) and your cold wallet (used for secure storage) separate. The cold wallet should never interact with any address other than the hot wallet's.
Hardware wallets (Ledger, GridPlus, Trezor) can greatly help with security by requiring you to approve of each transaction individually on the hardware wallet.
Hardware wallets store the seed and keys, so the software client will never have them and can’t leak them.
When the MyAlgo online wallet was hacked in Feb 2023 due to attackers inserting code into the client code (through the equivalent of a supply chain attack), hardware wallets were mostly safe. The attacker could trick the hardware wallet into signing an arbitrary transition, but it could not steal the seed or private keys.
Use 2FA/MFA: Every one of your centralized accounts for CEXs and mobile apps should have 2FA. They need at least 2 out of the 3 following:
something you Know: password passcode
something you Have: OTP from an authenticator (more secure), OAuth from another login IdP, or a mobile SMS (not recommended and not secure due to SIM Swaps). If you're using SMS 2FA for crypto, you need to switch that out for OTP immediately.
something you Are: fingerprint, biometrics
Keep your seed phrase secure:
Never give away your seed phrase. Legitimate services other than wallets will NEVER ask for your seed phrase. NEVER.
Be very careful about where you transmit or store a seed phrase. If it ever gets stolen, you've lost that account and every private/public key derived from it. Every address in that wallet, even if some are protected by a hardware wallet, is lost.
Do not Store your keys online. We’ve had people lose their wallet due to keeping it in Evernote, which isn’t safe at all from their employees. Even online password safes like LastPass (hacked 3 times in a decade) are not safe for storing your keys.
Make sure your devices are secure. Malware on your computer or mobile device can easily read your memory's clipboard and steal your seeds/passwords. Bad browser extensions can do the same. Consider using a separate browser or browser profile just for your crypto. Use anti-malware software and keep your devices clean.
Disaster planning
Have redundant backups for all your seeds and logins.
Disaster recovery simulations. If your phone and computer get stolen while you're traveling, can you still recover your accounts? If a fire breaks out in your home and destroys everything inside, can you recover your accounts?
Beneficiaries: If you disappear, are your beneficiaries able to access your cryptoassets?
Use test transactions
Send a test transaction for a small amount before sending a larger amount. Then check a blockchain explorer to see whether it worked properly. This won't catch all scams since some specifically trigger only with larger amounts or after your balance grows, but it'll prevent the majority of mistakes
1B - Intermediate Best Practices
Intermediate practices you should know
Do NOT approve of a transaction more than once. When approving a transaction, only press the approve button once. There is a common scam where a dApp will stack multiple transactions on top of each other. The first one is legitimate, but the rest aren't. If you press approve multiple times thinking the transaction didn't go through, you'll actually be approving multiple transactions.
Use a Contact list: Save commonly-used safe addresses in the wallet's contact list. Would protect against address poisoning.
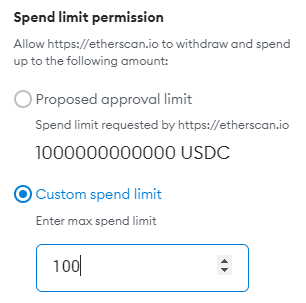
Set reasonable approval limits: Whenever you visit a Swap or a dApp, they usually require you to first send an "Approve" transaction to set a spending limit for tokens.
Most dApps use unlimited spending by default, which allows the approved address to take your tokens or any NFT collection at any time in the future with no restrictions. Contracts can have bugs or acquire some later if they're upgradeable. Don’t use the default proposed approval limit; press the Edit button and set your own limit.
Revoke approvals: It's good to periodically use a Token Approval Checker or revoke.cash to check which contracts have unlimited spending approval from your address. If you don't plan to use the dApp anymore, you should revoke the approval by setting the allowance back to zero (but note that it costs transaction fees).
When possible, use a desktop computer where you can better check for bad addresses, bad links, and bad signs. People tend to YOLO on mobile devices without doing due diligence.
Double-check every transaction on your wallet before approving of them. 90% of scams could be avoided if only people did this. Your wallet should provide you info on:
Absolutely double-check the value being sent and the recipient address
Nearly ALL honeypots scams require you to send some high value of native token to interact with them.
Used mixed-case checksum addresses.
Do not use shitty wallets that don't give details about the transaction.
If you're interacting with a contract:
If you see an Edit button on the transaction, click on it and check the details. That means certain parameters are being passed to a contract.
Double-check the contract address on a block explorer and see what it has done in the past. But be careful because block explorers can be exploited to show the wrong information for ERC-20 tokens.
If the gas-limit is ridiculously high, it means the transaction will fail due to one of the parameters or requirements being unmet.
Which parameters (e.g. approval limit, token ID, metadata, etc.) you're setting
Use Stelo to reveal what the transaction is actually doing. It's an extension that monitors for bad transactions
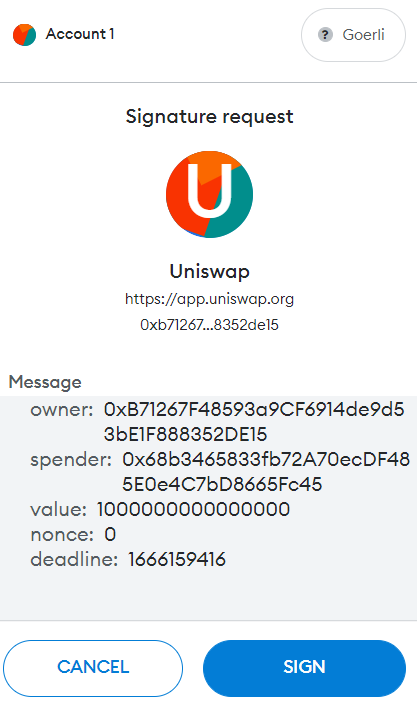
Do not sign signature requests if they look suspect
Signing welcome messages that ask for you to confirm your identity are almost always safe.
If Metamask gives you a red-text warning, it means you're signing an unknown transaction. If the signature request looks like a transaction hash, it's NOT safe. The creator of the signature can make you send any transaction.
If the signature request looks like an approval request, be aware that you’re giving that spender access to use your token (up to the allowance value).
1C - Advanced Best Practices
Anyone deep in DeFi should follow these recommendations, especially if they're early pioneers interacting with new projects.
Research every project first: This means using various sources: their documentation, media, social media forums, blockchain explorer, code analysis. If you're unable to do any of those, find someone trusted who has the expertise to do that for you. You shouldn't be diving into projects you haven't thoroughly researched.
Know how to analyze a block explorer
Find the contract on-chain. Check who interacted with it in the past and whether it worked for them.
Check the on-chain tokenomics
Trace some previous transactions
Be aware that blockchain explorers can be exploited. They rely on data provided by Emit/Events. Broken token contracts can make it look like any address is sending to another address even though the account balance is not updating, and even when the token sender didn’t make any transaction.
Know how to analyze code:
Crypto is not for everyone. If you're a DeFi pioneer interacting with projects that don't have a trustworthy doxed or known team, you need an expert to analyze the contract code.
Check that the source code is published with "Contract Source Code Verified" with "Exact Match". If not, avoid it unless you absolutely trust the developer. If it only says "Similar Match Source Code", it could have malicious constructor arguments.
If you're using Solana, Cardano (I don’t see a feature to upload source code), or Algorand (only shows decompiled code), you're out of luck unless you can acquire the contract code elsewhere and can compile it yourself. This is why I don’t trust DeFi on those networks. Those networks are not ready to operate trustlessly until their block explorers allow devs to upload their code for verification.
Part 2: Common Scam Tactics and Vectors of Attack
This section is divided into 2 parts:
Preparation: Phishing and deceit tactics used to coax the victim into the scam
Vector of Attack: The method used to steal the assets
2A - Preparation
Traditional methods: Spam email, social media messages, social engineering, sketchy Telegram/Discord channels. Tried and true methods that have been around forever.
The vast majority of crypto scams use traditional methods like social engineering. Both Pigs Butchering scams and the FTX/FTT scam are traditional scams.
Support scam is also common. If you ask for support help on Reddit subs or support forums, scammers will read those posts and private message you pretending to be support. As a general rule of thumbs, never interact with unknown messages.
We have also seen targeted messages where someone will raise an official MetaMask support ticket, and later they will get a scam email that only MetaMask support will know. The way this works is that MetaMask has a Zendesk ticketing system with many support agents, and all agents can view each other’s tickets. It only takes one bad actor to exploit their permissions and send you a fake email with the information they stole from the ticketing system.
Bait-and-Switch: A scammer attracts users to their dApp website and operates it legitimately for months. They can provide large rewards to attract as many customers as they can, operating at a small loss. Then one day, they suddenly switch out the logic of the dApp and use it to steal funds.
Many scam dApps and Rug Pulls use bait-and-switch tactics. An example where a liquidity pool worked fine for months and then suddenly stole all their user's funds.
The Squid Game contract was a Bait-and-Switch proxy contract that used an upgradeable contract. Switching its implementation logic to another contract prevented withdrawals.
Whaling: When you connect your wallet to any dApp, it asks to be able to see your balance for all your tokens. A malicious dApp could operate legitimately until the day they encounter a large whale. Only then do they switch the logic and steal funds from that whale. It makes it harder to detect attacks until it matters to them.
Mass marketing/social media: Scammers can also mass-market their scams using ads and social media. They can make a ‘free’ token airdrop or ICO announcement to attract new users. You see these all the time on reddit where a spammer will post on a dozen crypto subreddits at a time before getting blocked (like the recent Porsche NFT scam).
Random Airdrops: If you've been active on the Polygon PoS or BSC networks, you probably have a few random airdropped tokens or NFTs on your account. Those useless tokens usually leave a message to visit a scam website for more info. I personally have a dozen on my own accounts, many of which have purposely-misspelled domains of popular dApp sites.
Fake tokens with the same name (UNI example and details): Anyone can create a token with the SAME name as an existing token. The fake token contract can have a link to a fake website instead of the real one.
Address Poisoning: (Seen here and here and here. It’s becoming common.) This takes advantage of the fact that account addresses are long, and that you can generate public addresses that share the same starting digits as other addresses. The attacker monitors thousands of victims for their token-sending behavior. They create accounts with addresses that have the same starting characters as their victim and victim's recipient. They then transfer tokens of 0 amount to the victim's account and victim's recipient's accounts from the similar addresses. The attacker is hoping that in the future, the victims will reuse the attacker's addresses instead of the real addresses. Because the attacker is sending 0 tokens, it’s able to bypass the approval spending limit for most token contracts and fake transfers from the victim’s address to cause confusion.
2B - Vectors of Attack
Abuse the unlimited token approvals that they set for their own addresses. Nearly all swaps request for token approvals, and most use unlimited approvals. Whenever you give an address token approval, that address could use up to the allowance limit at any time in the future until you revoke that approval.
Many contract may contain undiscovered bugs
Proxy/Upgradeable contracts: Most contracts are immutable, but there are proxy contracts that store the value of a logical contract in a state variable. The proxy contract borrows/calls the functions in the logical contract for functionality. This allows them to be upgradeable by changing the address of the state variable. So even proxy contracts are safe now, they could have a bug or exploit in the future, like how the Squid Game token scam worked. (As a random side note, the r/CC MOON token and the Reddit collectible avatars NFTs also use proxy contracts.)
Low-liquidity Pump-and-Dump: Many scams tokens use low-liquidity to PnD. They create a new token, put a negligible fraction of it on the market, buy the token to pump the price. Due to low liquidity, it doesn’t take much to pump the price. As the retail traders buy more, they slowly mint more tokens and use the retail users as exit liquidity.
Stacking multiple transactions (Demo video): This is a fairly common method that is very easy to fall for, even for experienced crypto users. A dApp will send multiple transaction requests. Your wallet receives them. The first one you see is legitimate, so you confirm it. However, the Confirm button doesn't seem to have worked, so you press it again and again without double-checking. What you didn't realize was that there were multiple separate transactions, and the subsequent ones drained your wallet.
Request the wrong transaction. dApps can change the transaction request. They might send you an approve request followed by a send request. If you’re not paying attention in the wallet, you might no notice that the dApp’s second transaction request does something completely different than what the front-end says. It may say “Swap” in the website, but it’s actually another approve for a different contract and spender.
Deceiving Blockchain Explorers: Blockchain explorers have many vulnerabilities: https://harrydenley.com/bad-actors-abusing-blockexplorers-to-trick-you
NFT Drainers
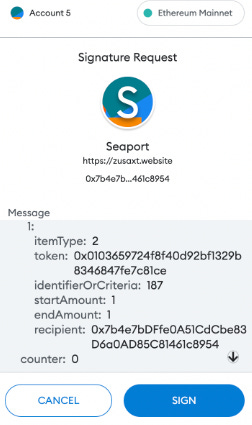
NFT drainers (there are a lot on github) rely on spoofed Signature Requests that impersonate an OpenSea/SeaPort signature request. You visit a fake NFT marketplace website, and they ask you to sign a gasless Seaport signature request using your wallet (see below). This signature is secretly an setApprovalForAll() transaction. Once signed, the attackers use the signature to drain all your NFTs from your account.
This type of scam was super-popular earlier in 2022.
MetaMask now shows a white warning when this happens, but people still ignore it or fail to check the recipient address like this monkey jpeg owner who lost 14 BAYCs in Dec 2022. Not every wallet will show a warning.
Broken Token and NFT Contracts
Token contracts are very loosely defined. Just because something technically qualifies as an ERC-20 token or ERC-721 NFT doesn't mean they're actually functional. Nodes and blockchain explorers only care that the function name and parameters sent to the function are of the correct variable types. Within those functions, anything goes.
Blockchain explorers will report that A has sent to B if an Emit/Event has been sent from a token contract. The details of that Emit/Event can be entirely made up. Spoofed token transfers happen all the time.
Blockchain explorers will update the balance of an account based on the balanceOf() function of the token contract. The details of that balanceOf function can be entirely made up. The details of the totalSupply variable can also be completely made up.
I can create a token contract that's incredibly broken:
Every time you try to send the token using transferFrom(), it mints new tokens at a random address. It then reports that it sent 9999 tokens from Vitalik's address to you even though neither of your actual token balances updated.
When you check your balance, it shows either 69.420 tokens or 420.69 tokens depending on the block number.
And as far as the blockchain explorer is concerned, this is still a valid ERC-20 token.
Some scam tokens only allow the token owner to sell, or have a high tax that everyone pays like this MetaFarm DAO contract. Here’s one in a rug pull that allows the owner to arbitrarily increase his own balance.
Honeypots
Wallet Seed Phrase Honeypot
The scammer either sends his seed phrase to the victim or drops it in plain sight. The victim tries to steal the funds from the wallet but gets caught in a honeypot. Usually the account has no gas tokens, so the victim has to first send gas tokens to the address, which quickly gets stolen. There are 2 ways you can get trapped:
1) The moment you send gas to the wallet, a [sweeper bot](https://metamask.zendesk.com/hc/en-us/articles/5716855323675-Fighting-back-against-sweeper-bots) empties the funds in that wallet before you can do anything. These bots are constantly scanning the mempool and operate faster than you can refresh the blockchain explorer page.
2) The account is a multiSig or requires another account to sign before funds can be transferred.
Github and Copy-paste code Honeypots:
I've seen these several times on Github and other code bases. Someone posts code of how to do something complex like execute a flash loan, create an NFT marketplace, or create a front-running bot. They tell the victim that it's super easy as long as they follow their "step-by-step guide that anyone can do". It preys on the victim's greed. The contract secretly contains a vulnerability, usually executed in the contract's constructor.
One popular variation (seen here, here, and here) secretly imports code from outside of the contract where a "Manager" contract sends the user's fund to another address.
Developer Honeypots:
There's a whole category of honey smart contracts made by devs that target other devs. Basically, there is an intentional bug or vulnerability in a honeypot contract holding some tokens to bait a developer into attacking it. However, there is a 2nd vulnerability in the contract that's much harder to find that traps the attacker. They're quite technical, so I've posted more details about them in another article here.